Tenable supports software inventory management through asset discovery, vulnerability scanning, and compliance auditing, complementing other IT systems for comprehensive asset management.
This article explores whether Tenable can handle software inventory and how it can be integrated into a broader cybersecurity strategy.
Understanding the Importance of Software Inventory:
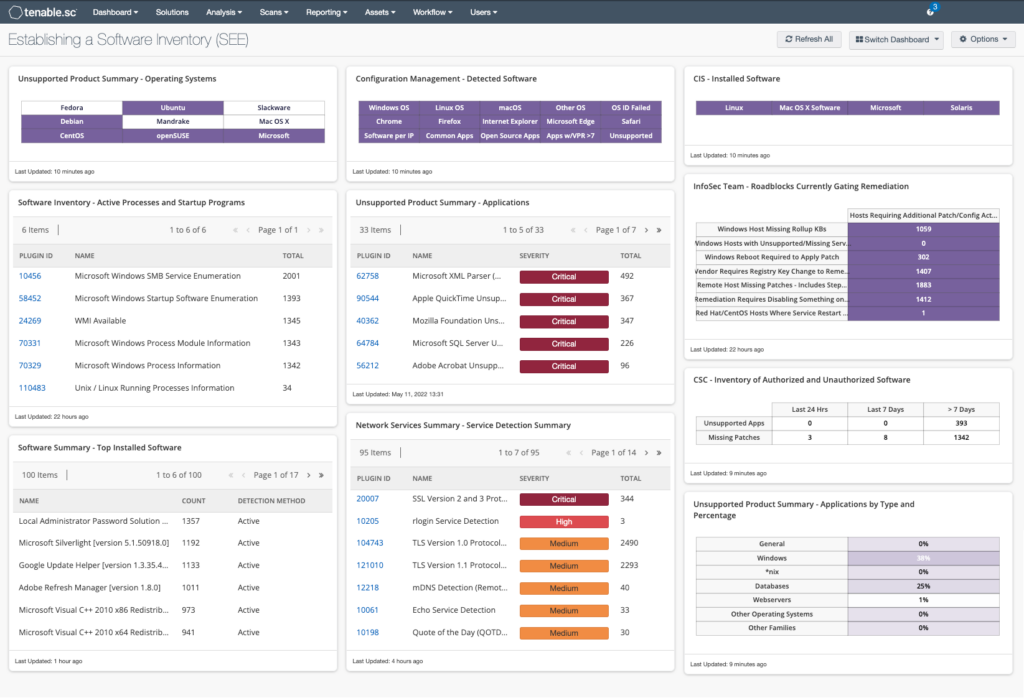
Software inventory is the systematic tracking of all software assets within an organization. This inventory includes every piece of software, ranging from operating systems and applications to utility programs and middleware. A detailed software inventory provides numerous benefits, including:
- Enhanced Security: Knowing what software is deployed across your network allows you to identify vulnerabilities, outdated software, or unauthorized installations that could be exploited by cyber attackers.
- Compliance Assurance: Regulatory frameworks often require organizations to keep precise records of their software to ensure compliance with legal standards such as GDPR, HIPAA, or SOX.
- License Management: Proper inventory management helps in tracking software licenses, avoiding fines for non-compliance, and ensuring that you’re not overpaying for unused licenses.
- Efficient IT Management: It simplifies the process of software updates, patches, and upgrades, ensuring that all systems run the latest and most secure versions.
Given these critical needs, the question arises: can Tenable, a platform primarily known for vulnerability management, effectively support software inventory tasks?
Tenable’s Core Capabilities: A Brief Overview
Tenable provides a suite of tools designed to help organizations manage and mitigate cybersecurity risks. Its flagship products include Tenable.io for cloud-based vulnerability management and Tenable.sc for on-premises security operations. These tools are primarily used for identifying vulnerabilities, monitoring network activity, and ensuring compliance with security standards.
Tenable’s core offerings include:
- Asset Discovery: Tenable can discover all network-connected devices, giving organizations visibility into what’s running on their infrastructure.
- Vulnerability Assessment: This involves scanning systems for potential vulnerabilities, misconfigurations, and outdated software, which are cataloged and assessed.
- Compliance Auditing: Tenable helps organizations meet regulatory requirements by auditing software and configurations against industry standards.
While these features are not explicitly designed for software inventory, they provide foundational elements that can contribute significantly to inventory management.
How Tenable Supports Software Inventory Management:
While Tenable is not a dedicated software inventory tool like SCCM (System Center Configuration Manager) or Lansweeper, it offers several features that indirectly support software inventory tasks:
Asset Discovery and Classification:
Tenable asset discovery capabilities allow it to identify all devices connected to the network. During this process, it also identifies the software running on these devices.
This automatic discovery includes information about operating systems, installed applications, and version details, which can form the basis of a software inventory.
Detailed Software and Version Tracking:
Tenable vulnerability scans provide detailed reports on the software installed across your IT environment. These reports include information on software versions, configurations, and potential security vulnerabilities.
By regularly scanning your network, Tenable ensures that your software inventory remains up-to-date, helping you identify unpatched or outdated software that could pose a security risk.
Integration with IT Management Tools:
Tenable integrates seamlessly with Configuration Management Databases (CMDBs) and other IT asset management (ITAM) tools. This integration allows organizations to cross-reference Tenable’s findings with existing software inventory data.
For example, if Tenable detects a software version that doesn’t match your CMDB records, it can trigger an update, ensuring your inventory is accurate and complete.
Compliance and Audit Reporting:
Tenable’s compliance auditing capabilities are crucial for maintaining an accurate software inventory. By comparing your installed software against industry standards and regulatory requirements, Tenable helps ensure that all software in your inventory complies with necessary regulations. This is particularly important for organizations in heavily regulated industries like finance, healthcare, and government.
Automated Alerts and Notifications:
Tenable can be configured to send alerts and notifications when it detects unauthorized software or when software falls out of compliance. This proactive approach helps organizations respond quickly to potential security issues or licensing violations, ensuring that their software inventory remains accurate and compliant.
Best Practices for Using Tenable for Software Inventory:
To maximize the effectiveness of Tenable in managing software inventory, organizations should consider the following best practices:
- Regular Scanning: Conduct regular vulnerability scans to ensure that your software inventory remains current. Tenable’s automated scanning capabilities can be scheduled to run at regular intervals, ensuring that all software changes are captured and recorded.
- Integration with CMDB: Leverage Tenable’s integration capabilities to connect with your existing CMDB or ITAM tools. This ensures that all discovered assets and software are automatically updated in your central inventory system.
- Compliance Monitoring: Use Tenable compliance auditing features to regularly check that all software in your inventory complies with relevant industry standards and regulations. This not only helps with regulatory compliance but also strengthens your overall security posture.
- Incident Response Planning: Incorporate software inventory management into your incident response plan. By knowing exactly what software is installed across your network, you can respond more effectively to security incidents, minimizing the impact on your organization.
Complementing Tenable with Dedicated Software Inventory Tools:
While Tenable offers valuable features that support software inventory management, organizations with complex IT environments may benefit from complementing Tenable with dedicated software inventory tools. These tools can provide more granular control over inventory management, including advanced reporting, license tracking, and automated deployment features.
Some popular software inventory tools that can complement Tenable include:
- Lansweeper: Offers comprehensive asset management and software inventory capabilities with detailed reporting and integration options.
- Microsoft SCCM: A powerful tool for managing large-scale software inventories, particularly in Microsoft-centric environments.
- SolarWinds Network Performance Monitor: While primarily a network monitoring tool, it also offers software inventory features that can be integrated with Tenable for a more complete view of your IT environment.
By combining Tenable with these specialized tools, organizations can achieve a robust and comprehensive software inventory management strategy that enhances security, compliance, and operational efficiency.
FAQ’s
1. Can Tenable perform software inventory management?
Yes, Tenable supports software inventory management by discovering and tracking software across network-connected devices, although it is not a dedicated software inventory tool.
2. How does Tenable help in managing software inventory?
Tenable helps manage software inventory by identifying installed software, tracking versions, and integrating with IT management tools like CMDBs for accurate data.
3. Is Tenable a replacement for dedicated software inventory tools?
No, while Tenable provides valuable features for software inventory, it is best used in conjunction with dedicated tools for more granular control and advanced reporting.
4. What are the key features of Tenable that support software inventory?
Key features include asset discovery, vulnerability assessment, compliance auditing, and integration with IT management systems.
5. Can Tenable integrate with other software inventory tools?
Yes, Tenable can integrate with tools like SCCM, Lansweeper, and SolarWinds to enhance software inventory management and ensure comprehensive IT asset visibility.
Conclusion
Tenable is a cybersecurity platform that, while not specifically designed for software inventory, supports it through asset discovery, vulnerability scanning, and compliance auditing. By integrating Tenable with dedicated software inventory tools, organizations can maintain an accurate and secure software inventory. This combination is vital for staying ahead of evolving cyber threats and ensuring compliance with industry regulations.